
Kim PepperCo-Founder & Tech Director
All PreviousNext Drupal 8 projects are now managed using Composer. This is a powerful tool, and allows our projects to define both public and private modules or libraries, and their dependencies, and bring them all together.
However, a if you require public or private modules which are hosted on GitHub you may run into the API Rate Limits. In order to overcome this, it is recommended to add a GitHub personal access token to your composer configuration.
In this blog post, I'll show how you can do this in a secure and manageable way.
It's common practice when you encounter a Drupal project to see the following snippet in a composer.json file:
"config": {
"github-oauth": {
"github.com": "XXXXXXXXXXXXXXXXXXXXXX"
}
},What this means is, everyone is sharing a single account's personal access token. While this may be convenient, it's also a major security risk should the token accidentally be made public, or a team member leaves the organisation, and still has read/write access to your repositories.
A better approach, is to have each team member have their own personal access token configure locally. This ensures that individuals can only access repositories they have read permissions for, and once they leave your organisation they can no longer access any private dependencies.
Go to https://github.com/settings/tokens and generate a new token.
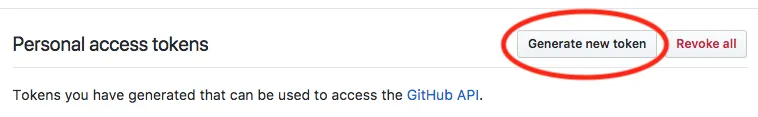
If you just need to bypass API rate limits, this token requires no scopes. If you need it to have access to private repos, you will need to specify all repo scopes.
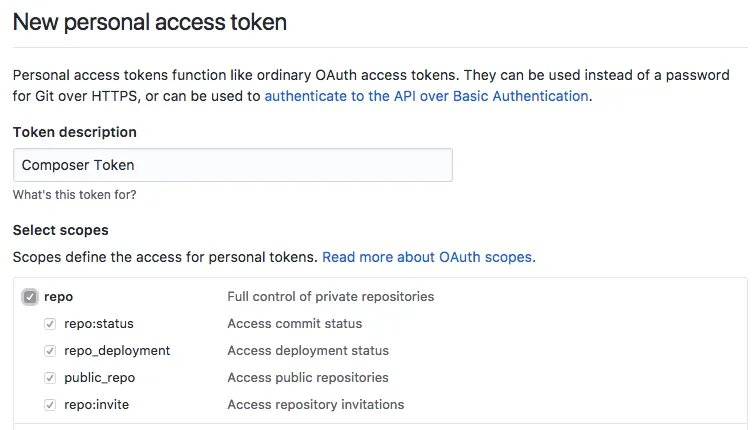
Finally, hit Generate Token to create the token.
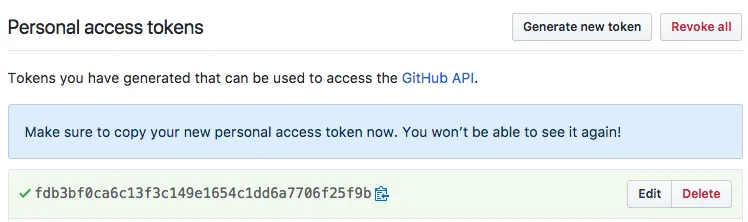
Copy this, as well need it in the next step.
Run the following from the command line:
composer config -g github-oauth.github.com XXXXXXXXXXXXXXXXXXXXXXX
You're all set! From now on, composer will use your own individual personal access token which is stored in $HOME/.composer/auth.json
Fortunately, composer also accepts an environment variable COMPOSER_AUTH with a JSON-formatted string as an argument. For example:
COMPOSER_AUTH='{"github-oauth": {"github.com": "XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"}}'You can simply set this environment variable in your CI Environment (e.g. CircleCI, TravisCI, Jenkins) and have a personal access token specific to the CI environment.
By using Personal Access Tokens, you can now safely remove any tokens from the project's composer.json file, removing the risk this gets exposed. You can also know that by removing access for any ex-team members, they are no longer able to access your organisations repos using a token. Finally, in the event of a token being compromised, you have reduced the attack surface, and can more easily identify which user's token was used.